As Hospitals and Medical Facilities extend wireless access, it is essential to develop a robust BYOD defense plan. The public nature of hospitals and the large traffic of visitors, professionals and staff increases the risk of exposing data, violating patient privacy, and malicious attacks. The recent attacks at Target and Neiman Marcus expose the sophisticated […]
Security and Longline Phishing Attacks
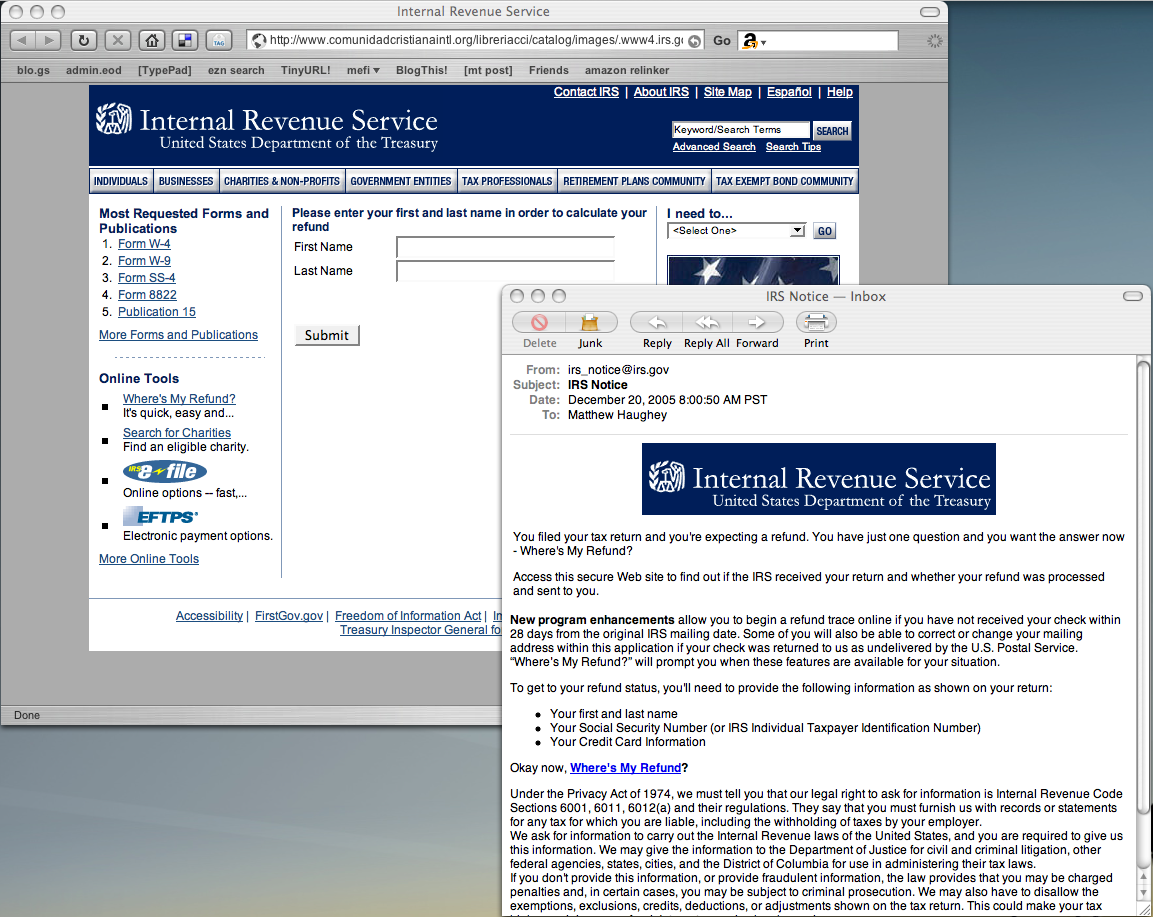
Just as new technologies are changing the workplace, new technologies and methodologies are also advancing among cybercriminals. The recent attacks at Target, Neiman Marcus and others utilized a combination of highly-sophisticated attacks that incorporated social engineering, parsing malware, and more. More and more businesses face the threat of advanced attacks like longline phishing. Proofpoint coined […]
Watching Email Subject Lines

According to a recent Websense report, phishing campaigns dropped to 0.5 percent in 2013 (from 1.12 in 2012), but the campaigns have also become more sophisticated and targeted. [1] Phishing emails lure the receiver to respond by clicking a link and giving personal information to what appears to be a trusted source. These campaigns are […]
The Four Phases of BYOD

Mobility is driving change in your organization whether you recognize it or not. In a recent press release, Gartner Research indicates that the utilization of mobiles devices will transform information security as we know it. [1] Some organizations are still attempting to ignore the BYOD issue, but it’s not going away. According to Gartner, the […]
Using Mobile Devices in SMBs

Even as businesses are still trying to figure out the BYOD challenge, employees are already using mobile devices in the workplace. The rapid rise of smartphones and tablets in the consumer market results in many employees and business owners using the same devices for the workplace. For many business, vital data as well as the […]
Business Continuity Training Best Practices

Business continuity training is an essential part of developing a business continuity plan. If you’ve taken the time to develop a business continuity plan, you’re ahead of many businesses. What about your staff? Are they ready as well? Is your staff ready to respond based on planned protocols in case of an emergency? In a […]
EHR and the Value of Workflow Analysis

Workflow analysis and redesign is an essential part of EHR planning and implementation. One link to poor adoption and poor satisfaction with EHR may be related to poor planning. Any EHR implementation requires change. Change is stressful and causes resistance. Without effective planning, changes may actually hinder workflow and create ineffective and time-consuming workarounds. “One important lesson […]
Reducing EHR Risk

Reducing EHR risk must be integrated into transition planning, implementation and follow-up in order to avoid EHR failure, according to Dean F. Sittig, Ph.D., professor, School of Biomedical Informatics at the University of Texas Health Science Center at Houston. “The potential consequences of an EHR failure become of increasing concern as large-scale EHR systems are […]
Small Data Centers for SMBs

As SMBs realize the need for processing, analyzing and protecting data, they face the challenge of effectively managing and developing a small data center within the organization. Managing a data center in an SMB context often means juggling a range of challenges like budget constraints, cultural boundaries and perceptions, and spacial limitations. IT World recently […]
Beware of Zombie Phones

Zombie phones could be bleeding your bottom line. What is a zombie phone? A mobile device that you thought was turned off or turned over to the employee, but your company is still being billed. This is more common than you might think. After auditing the phone usage and phone billing for several companies, Pankaj Gupta, […]

