A malvertising network has placed malevolent ads on over 700 domains including such major sites as Amazon, Youtube, and Yahoo. Malvertising is not new, but the current network dubbed “Kyle and Stan” by Cisco security researchers has clever techniques to to avoid detection and spread the attack on major domains. Companies can be vulnerable to the […]
Defending Against Insider Threats (Part 2)
Insider Threats can cripple an organization, but a multi-layered security strategy can reduce the likelihood of success. Some of the best practices for guarding against insider threats also apply a range of security issues. When developing your overall security plan, it is important to prioritize implementation as well as establish a ranking of most critical […]
Defending Against Insider Threats (Part 1)

In their “Common Sense Guide to Mitigating Insider Threats 4th Edition,” CERT provides an exhaustive set of recommendations for defending against insider threats. This raises the question, “Can a company actually defend against insider threats?” Insider threats can be stopped, but it will require a layered approach throughout the company. Like many security issues companies […]
What are Insider Threats?

The age-old risk of insider threats is making headlines. Insider threats are threats that arise from access to vital company information, goods, and/or networks. Insider threats are not limited to employees but could also arise from contractors, partners and anyone else who has vital access to goods, data, or networks. Consider some of the following […]
Does Your Website Deliver Customer Value?
Customer value asks the question, “Is it worth your customer’s time to visit your website?” Do you deliver the information they need in the way they can best use it? When applying customer value to your website, you consider usability questions, but you also look beyond usability to the large questions of user experience. User […]
Usability and Your Customer
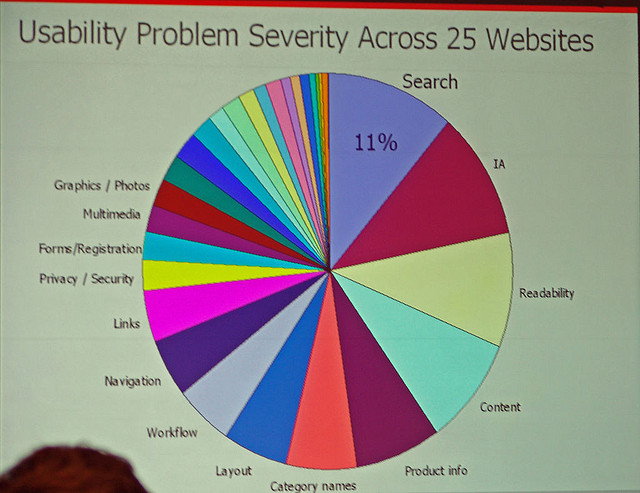
Usability plays a vital role in long-term engagement with your customer. If the tools, services, processes or website that the customer uses to interact with you are not easy to understand or easy to learn, then you may lose customers in the midst of the confusion. At some level every business, should consider all points […]
What is a DDoS Attack?
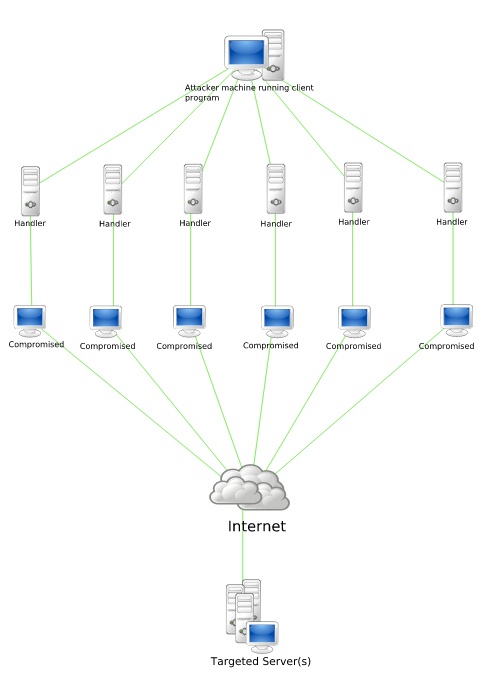
The speed and number of DDoS attacks have dramatically increased over the past few years. By some estimates DDoS attack occur at the rate of about 28 per hour. [1] A DDoS attack attempts to make a website or online service inaccessible by overwhelming the server using multiple sources of attack. The object of these […]
10 Smart Government IT Trends

In a recent symposium on smart government, Gartner Research analysts suggested that social, mobile, cloud and information are converging and driving innovation that will help establish and develop smart governments. Gartner offers 10 related IT trends that will play a key role in the coming years (see Gartner Newsroom). What is smart government? It might […]
Preparing for Bring Your Own Cloud

Bring your own cloud is fast emerging as a challenge that must be addressed. In some ways the challenges of BYOD (bring your own device) are connected to the challenge of bring your own cloud. The adoption of smartphones, tablets and other wireless devices has been accompanied by the rapid growth of customizable applications that […]
5 Levels of Mobile Security

Mobile security forms a key component of a business’s overall security strategy. The use of mobile devices impacts all size businesses from small to large, highlighting the need for a robust mobile security solution. Earlier this year, Gartner Research released a report listing five levels of mobile security that can help business conduct a assessment. […]

