Healthcare has continued to be a target for hackers in 2018. With continued threats from cyber criminals, it is crucial to take steps in order to better secure healthcare data and patient records. Reviewing previous cyber attacks can help you determine what not to do and learn from the mistakes of others. Here are highlights […]
Orangeworm Targeting Healthcare Data Security with Trojan.Kwampirs
Symantec released a late April 2018 report stating Orangeworm, a new cyber group, has been undermining healthcare data security with targeted attack campaigns against large healthcare firms and related industries using a custom backdoor malware known as Trojan.Kwampirs. Here’s what you need to know to stay on top of the developing IT health and security […]
Business Continuity Checklist: How to Reduce the Effects of IT Downtime
Business continuity solutions help a business quickly resume operations after downtime, effectively reducing breaks in business, lost data, and other associated consequences. A backup and disaster recovery (BDR) vendor can help you set up and manage this IT strategy, just make sure they offer the following business continuity features: Learn more about business continuity solutions […]
Step-By-Step Guide: How to Deal With a Security Breach
Unfortunately, security breaches are quickly becoming commonplace in our everyday lives. From Arby’s to social media platforms to America’s Job Link, data breaches of all shapes and sizes have made it clear that no business or organization is safe from hackers and other security threats. Just as clear as the danger, though, is the fact […]
Emergency IT Services in Knoxville, TN
IT problems can be a nightmare, especially for an unprepared business or non-profit organization. Whether it’s a downed network, a malware virus, or some other critical IT interruption, we understand that resolving your IT issue — so that you can get back to business or helping others — is of the utmost importance. If you […]
The Dangers of Using Public WiFi and Password-Protected Networks
Public WiFi and shared networks (like password-protected networks at work) are great ways to get work done away from home or amongst coworkers. But, did you know that using public WiFi and shared networks come with security risks? Here’s what we mean: The Risks of Using Public WiFi or Shared Networks When you’re on public […]
The Complete Laptop Buying Guide
Well, the time has finally come to replace your old, faithful laptop. Whether it finally bit the dust, or it’s simply not running like it used to, you’re on the market for a new computer. With so many options for operating systems, specs, and sizes, it can be overwhelming at first to find the best […]
The Pros and Cons of a BYOD Policy
BYOD, or Bring Your Down Device, is the name of a workplace policy that allows employees to bring their own laptops, tablets, and mobile devices for professional, work-related purposes. This can be advantageous to many businesses as it helps to cut costs on equipment and technology while increasing employee productivity. Although the cost responsibility is […]
Protection Against Malvertising

A malvertising network has placed malevolent ads on over 700 domains including such major sites as Amazon, Youtube, and Yahoo. Malvertising is not new, but the current network dubbed “Kyle and Stan” by Cisco security researchers has clever techniques to to avoid detection and spread the attack on major domains. Companies can be vulnerable to the […]
What is a DDoS Attack?
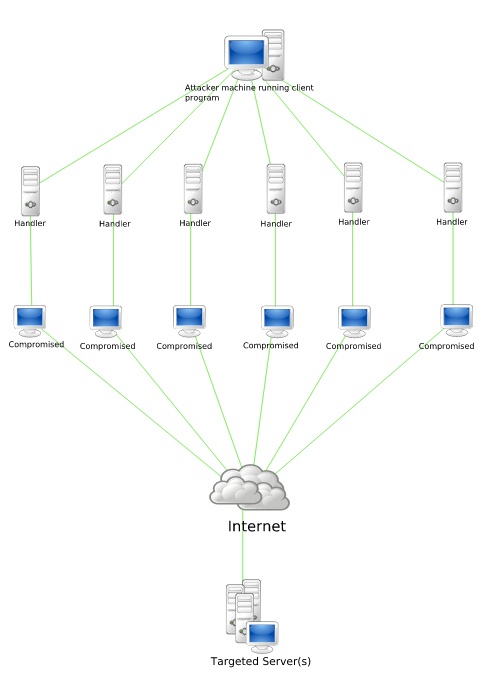
The speed and number of DDoS attacks have dramatically increased over the past few years. By some estimates DDoS attack occur at the rate of about 28 per hour. [1] A DDoS attack attempts to make a website or online service inaccessible by overwhelming the server using multiple sources of attack. The object of these […]
