There is such great importance in having a high quality and efficiently running security system installed in your technology system at work. I think we all know that by now. However, what makes Integracon’s premier IT managed security suite different from the rest? And how can this service be beneficial to you working from home […]
How to Avoid Viruses on Your Computer
Last week when we discussed how to backup your computer’s files, we talked about how losing your files in a computer crash (without having backed them up) is one of the most stressful events one can encounter with their gadgets. Today, we’re talking about another one of these stressful happenings — when your computer gets […]
The Pros and Cons of a BYOD Policy
BYOD, or Bring Your Down Device, is the name of a workplace policy that allows employees to bring their own laptops, tablets, and mobile devices for professional, work-related purposes. This can be advantageous to many businesses as it helps to cut costs on equipment and technology while increasing employee productivity. Although the cost responsibility is […]
Personal Online Security 101
It is estimated that around 30,000 websites are hacked per day. 1.5 million cyber attacks happen annually. And, if that’s not surprising enough, nearly two thirds of U.S. adults with social media accounts say that their accounts have been hacked. We all think, “I’m safe online. It won’t happen to me.” However, the truth is […]
Protection Against Malvertising

A malvertising network has placed malevolent ads on over 700 domains including such major sites as Amazon, Youtube, and Yahoo. Malvertising is not new, but the current network dubbed “Kyle and Stan” by Cisco security researchers has clever techniques to to avoid detection and spread the attack on major domains. Companies can be vulnerable to the […]
Defending Against Insider Threats (Part 2)
Insider Threats can cripple an organization, but a multi-layered security strategy can reduce the likelihood of success. Some of the best practices for guarding against insider threats also apply a range of security issues. When developing your overall security plan, it is important to prioritize implementation as well as establish a ranking of most critical […]
Defending Against Insider Threats (Part 1)

In their “Common Sense Guide to Mitigating Insider Threats 4th Edition,” CERT provides an exhaustive set of recommendations for defending against insider threats. This raises the question, “Can a company actually defend against insider threats?” Insider threats can be stopped, but it will require a layered approach throughout the company. Like many security issues companies […]
What are Insider Threats?

The age-old risk of insider threats is making headlines. Insider threats are threats that arise from access to vital company information, goods, and/or networks. Insider threats are not limited to employees but could also arise from contractors, partners and anyone else who has vital access to goods, data, or networks. Consider some of the following […]
What is a DDoS Attack?
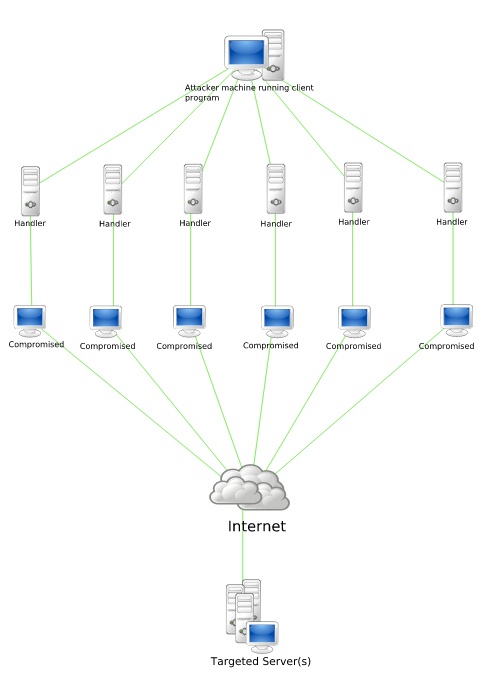
The speed and number of DDoS attacks have dramatically increased over the past few years. By some estimates DDoS attack occur at the rate of about 28 per hour. [1] A DDoS attack attempts to make a website or online service inaccessible by overwhelming the server using multiple sources of attack. The object of these […]
Avoiding Risky Security Habits

The recent Target and Neiman Marcus breaches should be a timely reminder for business leaders to invest in vigilant security habits. Unfortunately, many small to medium business may think of these rampant breaches as threats to the big companies. When it comes to security threats, no business is immune. Consumers in general, practice risky security […]
