If you thought the world was safe from vicious ransomware attacks after the WannaCry attack, and its subsequent patch, you were wrong.
On June 27, 2017, a possible strain of the Petya ransomware virus (which has been around since 2016) started propagating and infecting organizations in Ukraine, specifically Ukrainian government and business systems, before spreading internationally. This particular strain of ransomware, which according to Symantec may be a wiper rather than ransomware, is believed to have started in Ukraine in M.E.Doc accounting software, which then spread to more than 12,500 computers in Ukraine — all of which were running older versions of Microsoft Windows. Shortly after that, the virus spread to 64 other countries, as well as many well known private companies. Along with two other methods that helped it spread, it “used the same National Security Agency hacking tool, Eternal Blue, that was used in the WannaCry episode.”
Petya vs. NotPetya vs. Goldeneye
Strictly speaking, the June 27, 2017 ransomware attack was not done by Petya malware — it just initially looked like it. When the June 27, 2017 attack occurred, security researchers noticed a significant amount of shared code between the older Petya and the piece of malware currently affecting machines. After further digging they noticed, however, that those resemblances were only skin deep. Realizing this was something different, researchers at Russia’s Kaspersky Labs renamed the current malware “NotPetya.” Other variations of the name — Petna, Pneytna, etc. — have emerged since, along with totally different monikers, like Goldeneye (from Romania’s Bitdefender).
How NotPetya Is Different Than Typical Ransomware
Like most ransomware, NotPetya encrypts files and demands payment ($300 bitcoin) for the supposed release of files— but it doesn’t stop there. NotPetya also “encrypts and locks entire hard drives” (as opposed to other ransomware only locking individual files), it overwrites and encrypts the master boot record (MBR)…and it doesn’t have a kill switch.
During the WannaCry attack, a specific piece of code was found that led users to the kill switch — a move that effectively halted the continued spread of the WannaCry virus (for now). NotPetya doesn’t have a kill switch, which is why Matthieu Suiche, the security researcher who set up the WannaCry kill switch, says NotPetya is “an improved and more lethal version of WannaCry.”
How NotPetya Infects and Spreads
NotPetya is a worm, which means it can self-propagate. It spreads through computers by first building a list of target computers via IP addresses — both local area networks (LAN) and remote IPs. Once the target computers are identified, NotPetya gathers user credentials (like usernames and passwords stored in memory) to spread to the targets. Next, NotPetya attempts to spread laterally across networks, and to target computers, by copying itself (using legitimate tools) or using SMB exploits like EternalBlue or EternalRomance.
Once in a computer system, NotPetya encrypts files and continues to spread to other users. It goes through user-mode encryption, where files ending in a specific file extension are encrypted. It also modifies the master boot record (MBR) in order to “hijack the normal loading process of the infected computer during the next system reboot” (the reboot itself is scheduled at a later time to allow the infection to continue to spread within the network). The modified MBR then helps the virus encrypt the hard disk during a simulation of a Windows utility CHKDSK (“check disk”) screen. It is at this point that the system is being encrypted, after which a user would see the ransom note.
How to Respond to NotPetya Ransomware
To help the malware spread, NotPetya waits about an hour before rebooting the machine; this scheduled reboot, as stated earlier, helps spread the ransomware to other machines on the network. However, NotPetya does its real damage (to your machine) during the rebooting phase — or when you see the fake CHKDSK screen (see below). According to @HackerFantastic, it is at that fake CHKDSK screen that you should turn off your computer immediately. If you don’t power back on, you might be able to save your files from being encrypted.
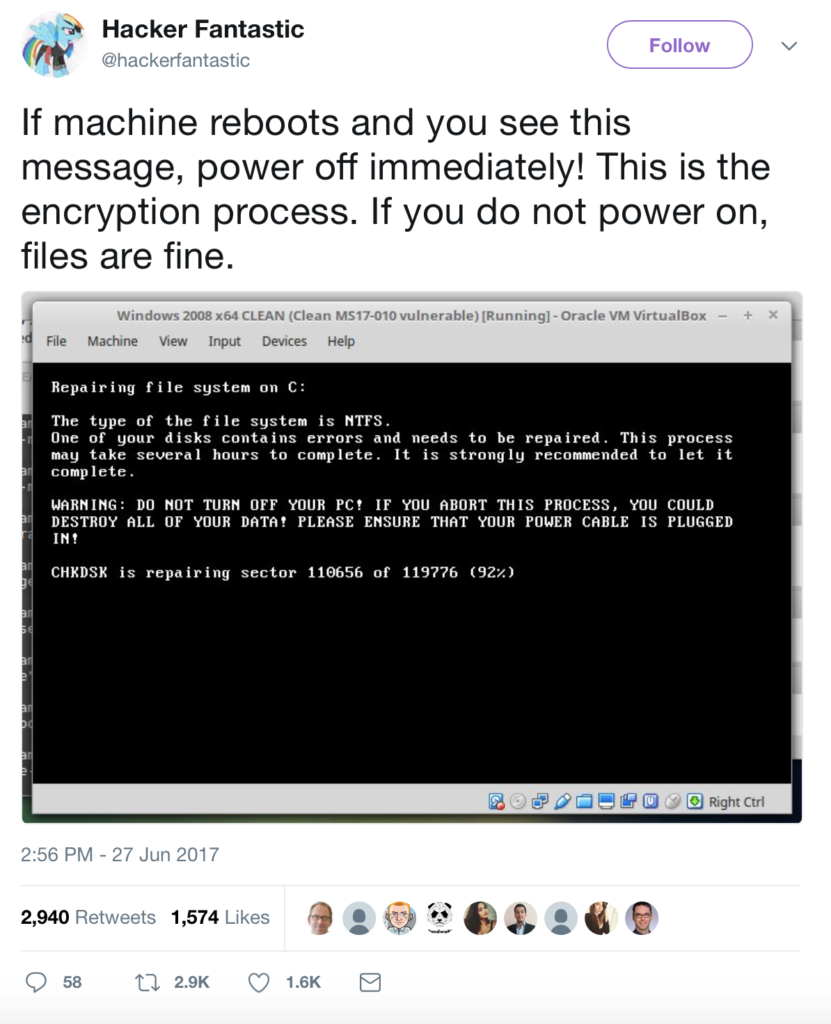
Source: @HackerFantastic
If you aren’t able to shut down your computer in time, here’s what you can do: “disconnect your [computer] from the internet, reformat the hard drive and reinstall your files from a backup.”
Don’t Pay the NotPetya Ransom
Security experts are warning users infected with NotPetya to not pay the ransom. Not paying the ransom will definitely cut down on the profitability of their “business,” but in the case of NotPetya, it’s unlikely that users will even get the decryption key to unlock their files anyway. That’s because the attackers’ single source of communication — an email address — was shut down by the email provider once they realized what it was being used for. Without that one way to communicate with the attackers, victims have no way to request the decryption key after paying.
Protecting Yourself from Ransomware
Protect your personal or company computers from ransomware, like NotPetya, by keeping a regular backup of your files. Secondly, be diligent about installing updates from your software and antivirus programs, especially Windows — these often contain patches to protect your system from malware attacks. Next, make sure your employees are educated about malware — including what to avoid, how to spot it, and what actions to take.
Finally, if you’re bad about updating your programs, or you just hate thinking about the constant burden that is your company’s IT maintenance and cyber protection, give Integracon a call. We specialize in creating and maintaining customized security suites for companies, effectively giving you peace of mind and more time to focus on your business.




