A malvertising network has placed malevolent ads on over 700 domains including such major sites as Amazon, Youtube, and Yahoo. Malvertising is not new, but the current network dubbed “Kyle and Stan” by Cisco security researchers has clever techniques to to avoid detection and spread the attack on major domains. Companies can be vulnerable to the […]
Defending Against Insider Threats (Part 2)
Insider Threats can cripple an organization, but a multi-layered security strategy can reduce the likelihood of success. Some of the best practices for guarding against insider threats also apply a range of security issues. When developing your overall security plan, it is important to prioritize implementation as well as establish a ranking of most critical […]
Defending Against Insider Threats (Part 1)

In their “Common Sense Guide to Mitigating Insider Threats 4th Edition,” CERT provides an exhaustive set of recommendations for defending against insider threats. This raises the question, “Can a company actually defend against insider threats?” Insider threats can be stopped, but it will require a layered approach throughout the company. Like many security issues companies […]
What are Insider Threats?

The age-old risk of insider threats is making headlines. Insider threats are threats that arise from access to vital company information, goods, and/or networks. Insider threats are not limited to employees but could also arise from contractors, partners and anyone else who has vital access to goods, data, or networks. Consider some of the following […]
What is a DDoS Attack?
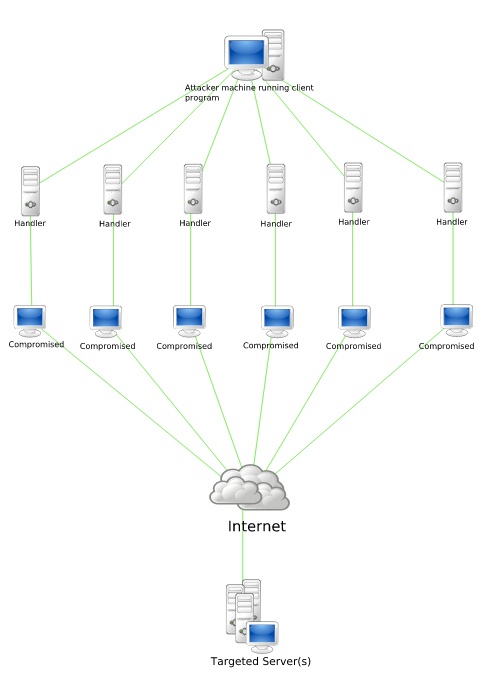
The speed and number of DDoS attacks have dramatically increased over the past few years. By some estimates DDoS attack occur at the rate of about 28 per hour. [1] A DDoS attack attempts to make a website or online service inaccessible by overwhelming the server using multiple sources of attack. The object of these […]
Preparing for Bring Your Own Cloud

Bring your own cloud is fast emerging as a challenge that must be addressed. In some ways the challenges of BYOD (bring your own device) are connected to the challenge of bring your own cloud. The adoption of smartphones, tablets and other wireless devices has been accompanied by the rapid growth of customizable applications that […]
Master Data Management Offers 360-degree Customer View

Successful CRM optimization will require a commitment to Master Data Management according to a recent press release from Gartner Research. In fact, Gartner goes so far as to say that CRM leaders who fail to invest in MDM will suffer up to 25 percent loss in potential gains by 2017. A thorough commitment to MDM […]
Avoiding Risky Security Habits

The recent Target and Neiman Marcus breaches should be a timely reminder for business leaders to invest in vigilant security habits. Unfortunately, many small to medium business may think of these rampant breaches as threats to the big companies. When it comes to security threats, no business is immune. Consumers in general, practice risky security […]
Security and Longline Phishing Attacks
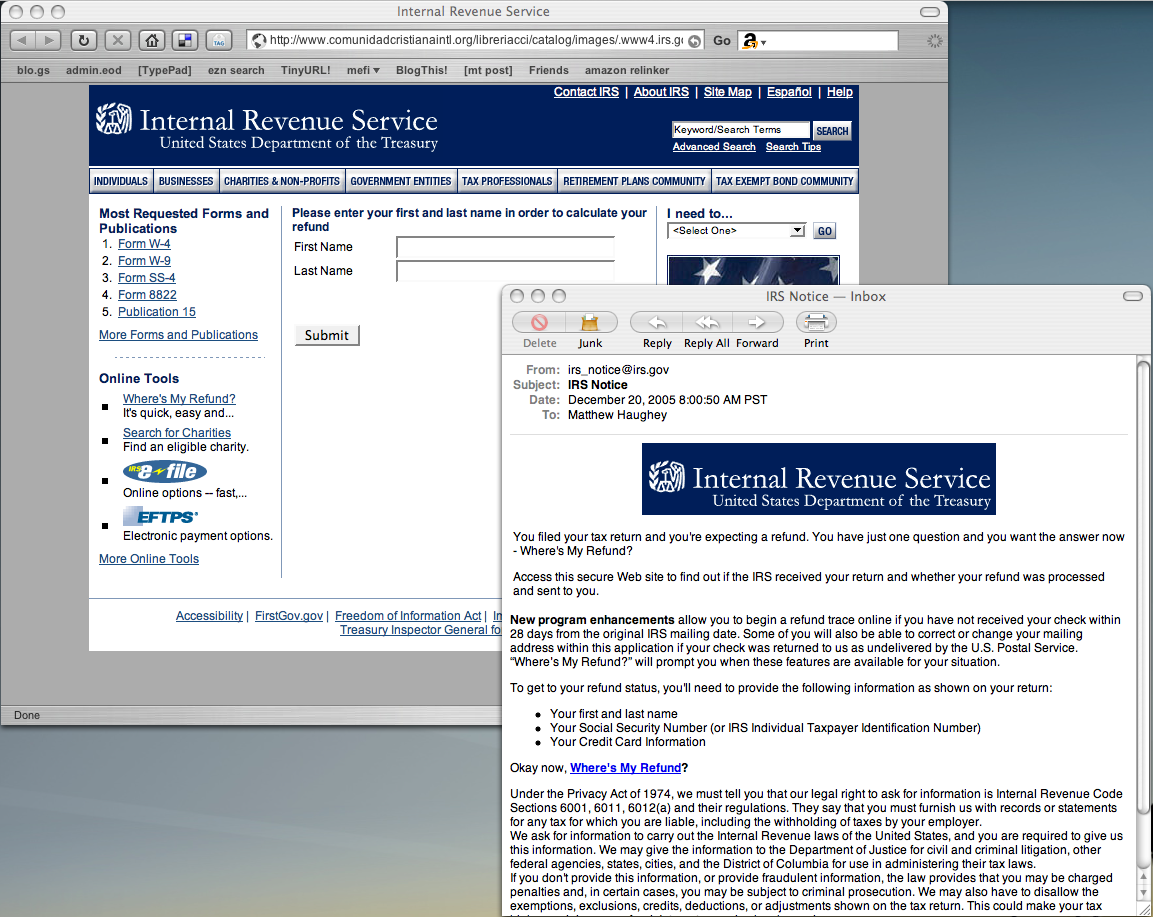
Just as new technologies are changing the workplace, new technologies and methodologies are also advancing among cybercriminals. The recent attacks at Target, Neiman Marcus and others utilized a combination of highly-sophisticated attacks that incorporated social engineering, parsing malware, and more. More and more businesses face the threat of advanced attacks like longline phishing. Proofpoint coined […]
Watching Email Subject Lines

According to a recent Websense report, phishing campaigns dropped to 0.5 percent in 2013 (from 1.12 in 2012), but the campaigns have also become more sophisticated and targeted. [1] Phishing emails lure the receiver to respond by clicking a link and giving personal information to what appears to be a trusted source. These campaigns are […]

