As Hospitals and Medical Facilities extend wireless access, it is essential to develop a robust BYOD defense plan. The public nature of hospitals and the large traffic of visitors, professionals and staff increases the risk of exposing data, violating patient privacy, and malicious attacks. The recent attacks at Target and Neiman Marcus expose the sophisticated […]
Technology Adoption and Utilization in Healthcare

Technology adoption and utilization remains one of the primary challenges facing practicing physicians according to The Physicians Foundation, a non-profit seeking to advance the work of practicing physicians and help facilitate the delivery of healthcare to patients. In their 2014 watch list The Physicians Foundation has listed five critical challenges facing practicing physicians. Practice and Insurance […]
Making Big Data Pay

Successful business leaders are learning ways to leverage big data within the organization. According to an independent study by the the Economist Intelligence Unit, the business landscape is dramatically changing based on the massive level of data being collected each daily. While effective use of big data can be daunting, some businesses have effectively utilized […]
Security and Longline Phishing Attacks
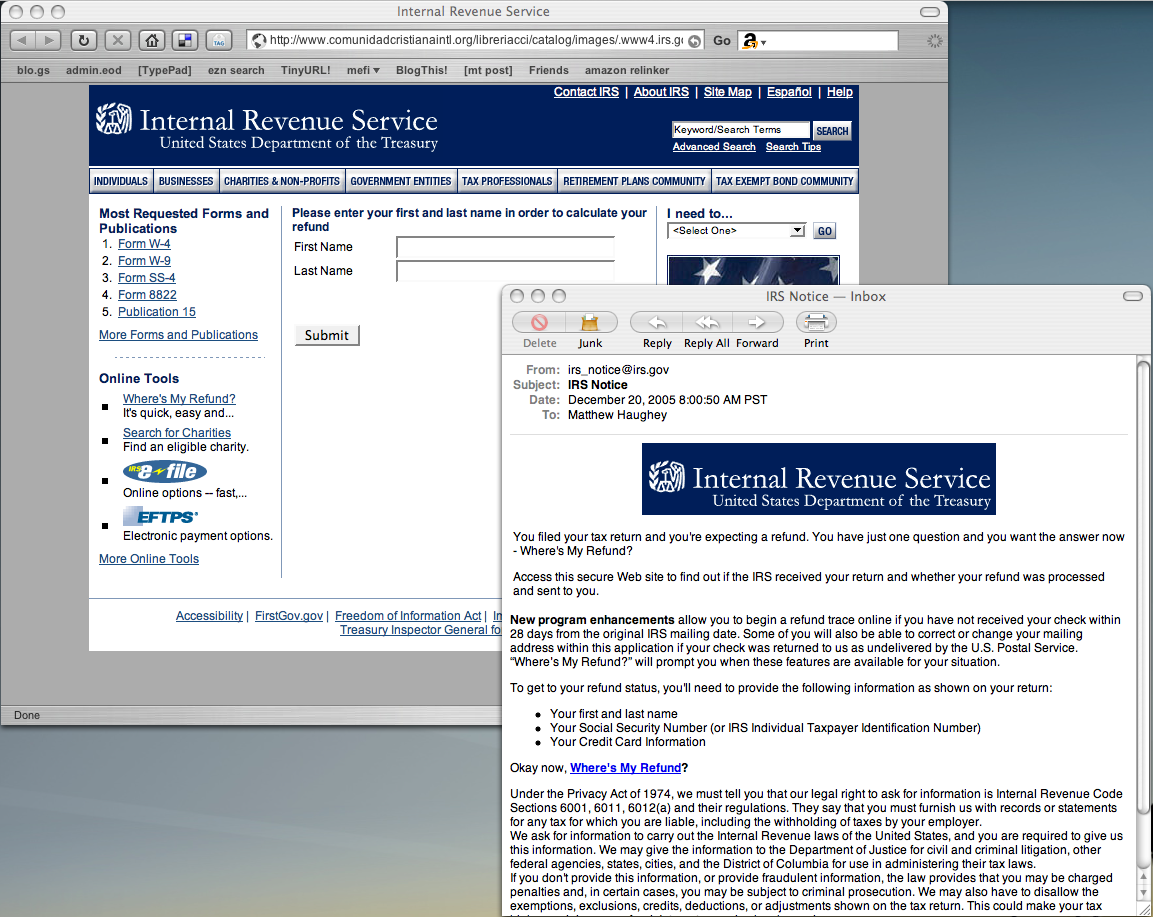
Just as new technologies are changing the workplace, new technologies and methodologies are also advancing among cybercriminals. The recent attacks at Target, Neiman Marcus and others utilized a combination of highly-sophisticated attacks that incorporated social engineering, parsing malware, and more. More and more businesses face the threat of advanced attacks like longline phishing. Proofpoint coined […]
Four Steps in Transforming Your Digital Strategy

Developing an integrated digital strategy can play a key role in planning your business’s long-term future. It not only helps align your technology investment strategy, it may may also help you consider the future of processes and product/service lines within your business. As your business considers developing an integrated digital strategy, McKinsey & Company suggests […]
Developing an Integrated Digital Technology Strategy

What’s your digital technology strategy? While businesses from large to small use technology in almost every level of business, not many business think in terms of an integrated digital technology strategy. The analysts at McKinsey & Company developed an digital technology matrix that can help businesses think about how technology is integrated at every level […]
9 Out of 10 Mobile Apps are Vulnerable

According to a recent HP Research Report, nine out of 10 mobile apps have vulnerabilities that could pose a security threat. HP Security Research tested a representative sampling of mobile applications that included reviewing the security of 2,107 applications by 601 companies listed in the Fortune Global 2000.[1] About 97 percent of the mobile apps […]
Offering Seniors Digital Health Tools

Seniors are increasingly interested in utilizing digital health tools to manage their healthcare. According to a recent study by Accenture 57 percent of American seniors are interested in using digital options for managing their health services remotely.[1] Currently only about one-third of medical facilities are offering digital health tools. How are senior adults interested in […]
Watching Email Subject Lines

According to a recent Websense report, phishing campaigns dropped to 0.5 percent in 2013 (from 1.12 in 2012), but the campaigns have also become more sophisticated and targeted. [1] Phishing emails lure the receiver to respond by clicking a link and giving personal information to what appears to be a trusted source. These campaigns are […]
The Four Phases of BYOD

Mobility is driving change in your organization whether you recognize it or not. In a recent press release, Gartner Research indicates that the utilization of mobiles devices will transform information security as we know it. [1] Some organizations are still attempting to ignore the BYOD issue, but it’s not going away. According to Gartner, the […]

