What is a Domain?
Domain names are identification strings that define a realm of administrative autonomy, authority, or control within the Internet — they either represent an Internet Protocol (IP) resource (i.e. a personal computer accessing the Internet), a server hosting a website, the website itself, or other services that communicate through the Internet. Domain names are organized in a hierarchy of subdomains in something called the DNS root domain and include top-level domains (TLDs), second-level domains, and third-level domains.
What is a Top-Level Domain?
While the second and third-level domains are typically open to being reserved by end users connecting with local area networks, run websites, or create publicly accessible internet resources, top-level domains — such as .com, .net, .edu, and .org — are the prominent domains that you are likely most familiar with. Top-level domains, including generic top-level domains (gTLDs) and country code top-level domains (ccTLDs), are considered the highest-level domain names of the Internet and the Domain Name System.
In 2009, there were 21 generic top-level domains and 250 two-letter country code TLDs. By 2016, there were 1000 live gTLDs. Today, there are more than 1,500 TLDs.
You can find an annotated list of TLDs in the DNS root zone database via the Internet Assigned Numbers Authority (IANA).
Suspicious Top-Level Domains
While domain names are an important way to establish a unique identity, easily recognize and memorize names to numerically addressed Internet resources, and to make network moves possible (globally or locally via an intranet), they’re also susceptible to abuse —they’re often the targets of scammers and hackers seeking to “game the system” by creating malicious sites, spammy emails, and malvertising that lead to phishing attacks and malware downloads.
Most new TLDs have been created in recent years in response to a higher demand from advertisers and domain speculators; however, their availability and low prices make them extremely popular among spammers and scammers. In fact, many of the cheapest, top-ten “bad” TLDs sell for $6 and $14.50 per domain, while some go for as low as 48 cents and a dollar each.
“…security experts warned that an onslaught of new, far cheaper TLDs would be a boon mainly to spammers and scammers.” (Krebs on Security)
Currently, the worst TLD is .men with Spamhaus saying 55% of the 65,570 registered .men TLDs are “bad.” Now, you may be thinking you’ll never intentionally visit a .men site, one of the other shady TLDs from the following lists, or click a spammy .party domain in an email — but you may still be fooled! That’s because the bad TLDs are often loaded only after a user clicks on a disguised and malicious link that originally doesn’t look so phishy — such as a .com or .org link.

Source: “The Most Abused TLDs” by Spamhaus.
Every year, Symantec publishes their top 20 list for shady TLDs, most recently 2018’s Top 20 Shady TDLs, in the hopes of shedding some light on the problem — by making TLD registries and independent users aware of the problem. Their lists are fluid (rankings of suspicious TLDs can vary from quarter to quarter).
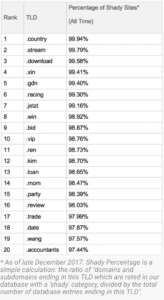
Source: “The Top 20: Shady Top-Level Domains” by Symantec.
Protect Your Business From Bad TLDs
Company-wide IT policies that follow IT best practices go a long way in ensuring your company isn’t affected by bad TLDs. Support from IT professionals, however, help you go the extra mile by implementing procedures that correctly block TLDs, educate your staff, and protect your valuable and often irreplaceable data.




